Standardisation organisation ETSI has published a new standard for identity proofing. Special is that it considers all different types of identity proofing.
In the wake of the revised eIDAS regulation, the standardisation organisation ETSI has recently published a new standard for identity proofing (ETSI TS 119 461 V1.1.1, 2021-07). Special in this standard is that it considers all different types of identity proofing, from physical registration at a counter to remote identity verification.Inverid gave feedback on the draft version and it is good to see it reflected in the final specification.

The aim of this standard is to meet the general requirements of the international community to provide trust and confidence in electronic transactions. It includes applicable requirements from the European eIDAS regulation and other areas such as know-your-customer (KYC) processes in various industries. The specification poses policy and security requirements specific to identity proofing covering applicable technologies and use cases.
ReadID can meet the relevant ETSI requirements easily. Optical solution providers will struggle to comply with the identity proofing requirements
I’ll discuss the new standard from three different perspectives: the identity proofing perspective, the ReadID perspective and the compliance perspective.
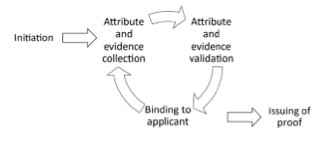
From an identity proofing perspective, I think ETSI did a great job as the specification clearly decomposes the whole identity process by breaking it down into five tasks:
- Initiation,
- Attribute and evidence collection,
- Attribute and evidence validation,
- Binding to applicant, and
- Issuing of identity proofing result.
Requirements are posed for each of these tasks whilst taking into account that the identity proofing can be done physically, remotely or a combination of the two. The authoritative evidence presented can be a physical identity document, digital identity document, eID means used in an authentication protocol (including digital identity wallets as foreseen in the proposed amendment of the eIDAS regulation), or a digital signature supported by a certificate. The specification defines the requirements for each combination of possibilities.
From a ReadID perspective, the specification clearly shows that NFC-based solutions are more secure than optical solutions to verify the authenticity of identity documents. ReadID can meet the relevant requirements easily. Optical solutions struggle with the verification of the authenticity of the identity document shown. A single picture of the document does not suffice anymore. Instead, a short video of the document must be recorded to allow for a better inspection of the validity of the document (requirement VAL-8.3.3-04). To make this point explicit: using a single photo is still a quite common industry practice, and this thus does not meet the ETSI requirements.
I am also happy that the requirements for physical identity proofing are finally made explicit. Physical or on-premise identity proofing is generally viewed as a benchmark for other solutions. Now it is possible to compare, for instance, remote solutions with physical presence solutions in terms of assurances. It is a pity, however, that biometrics-based solutions for remote identity proofing have to fulfil to some industry best practice threshold for false acceptances while this is not the case for physical proofing. Why not also specify some best practice threshold for physical desk-based identity proofing processes, e.g. as an outcome of the mandatory annual training (requirement VAL-8.3.3-15)?
That also brings me to the third and last perspective: compliance. As a compliance officer, I struggle a lot relating the ETSI requirements to the eIDAS levels of assurance Substantial and High for authentication solutions and to the requirements for the issuance of eIDAS qualified digital certificates. The specification offers a lot of room for interpretation. For example: what is the current industry best practice for false acceptance rates at Substantial, High or Qualified (requirement BIN-8.4.3-07)? And: in a physical identity proofing process, how many security features of an identity document have to be checked for Substantial, High or Qualified (VAL-8.3.3-07)? Or: what to do when NFC-based passive authentication is successful and clone detection fails whereas biometrics-based holder verification is successful? It will be a big challenge for a conformity assessment or supervisory body to say something meaningful about this with regard to assurance levels. Time will tell if Inverid is going to include it within the scope of its eIDAS module certifications for qualified trust services or electronic identification.
To summarising, ETSI TS 119 461 provides a well-structured and complete overview of all possible identity proofing processes and technologies. Further guidance and concreteness is required to make it really useful for solution providers and their conformity assessment and supervisory bodies. After all, at the end of the day, the relying parties, such as banks, trust service providers and governments, must be able to rely on identity proofing solutions and that want to know where they stand in terms of assurance. Obviously, such extra translation of the specification must evolve in time according to industry best practices to prevent that it becomes a rapidly outdating technical overview of identity proofing solutions.










